Now Days it is very convenient to use Remote Desktop Protocol(RDP) for accessing remote system over Internet, specially server systems(either client to server or server to server), although it is very convenient and easy way to access remote systems but it may cause big loss as it may provide an opportunity for remote attackers to guess logon credentials of client.
There may present many ways to prevent this but SSH keys Authentication provide an easy, and extremely secure way of logging into your server. For this reason, it is recommend use SSH keys Authentication for connecting with your remote server.
What is SSH :
Before configuring SSH Key Authentication we should know what is SSH, So here is the brief introduction to SSH:
SSH stands for Secure Shell also known as Secure Socket Shell,it is a network protocol that provides users a secure way to access a remote computer. Secure Shell provides strong authentication and secure encrypted data communications between two computers connecting over an insecure network such as the Internet.
How Do SSH Keys Work:
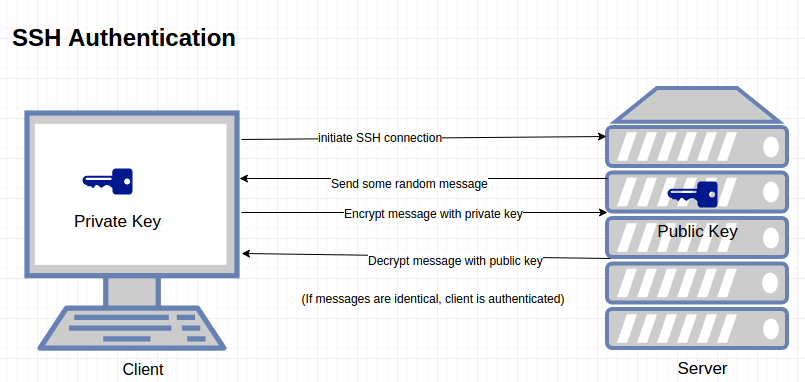
SSH key pairs are two cryptographically secure keys that can be used to authenticate a client to an SSH server. Each key pair consists of a public key and a private key to encrypt and decrypt data.
Public Key: Large numerical value that is used to encrypt data that only the private key can decrypt. The public key is uploaded to a remote server that you want to be able to log into with SSH.
Private Key: A private key (secret key) is a variable that is used with an algorithm to encrypt and decrypt code. Private key kept at client side. the key can be encrypted on disk with a passphrase.
Steps to Configuring SSH key Authentication:
For configuring ssh key authentication you should have public-private key pair. If you don’t have key pair then generate it by following commands.
Command for generating key pair:
Provide file name where you want to save the keys(you can leave it blank)
Enter passphrase to encrypt your private key (if you are providing any passphrase you have to remember it and provide it at the time of connection with your remote server/system. Again no harm while leaving it blank )
Here you can see that your key has been created and saved.
/home/knoldus/.ssh/id_rsa: Contain your private key.
/home/knoldus/.ssh/id_rsa.pub : Contain your public key.
Install the public key in remote server:
We can use either scp or ssh-copy-id command to copy our public key file in our account on remote server. To do so use following commands.
Command for copying public key on server:
scp $HOME/id_rsa.pub RemoteServer :~/.ssh/authorized_keys.
Login without SSH key Authentication:
we have to login with our password which may be insecure .
Login with SSH key Authentication:
we don’t need to login with our password which is a secure way to login.